5.1 Overview
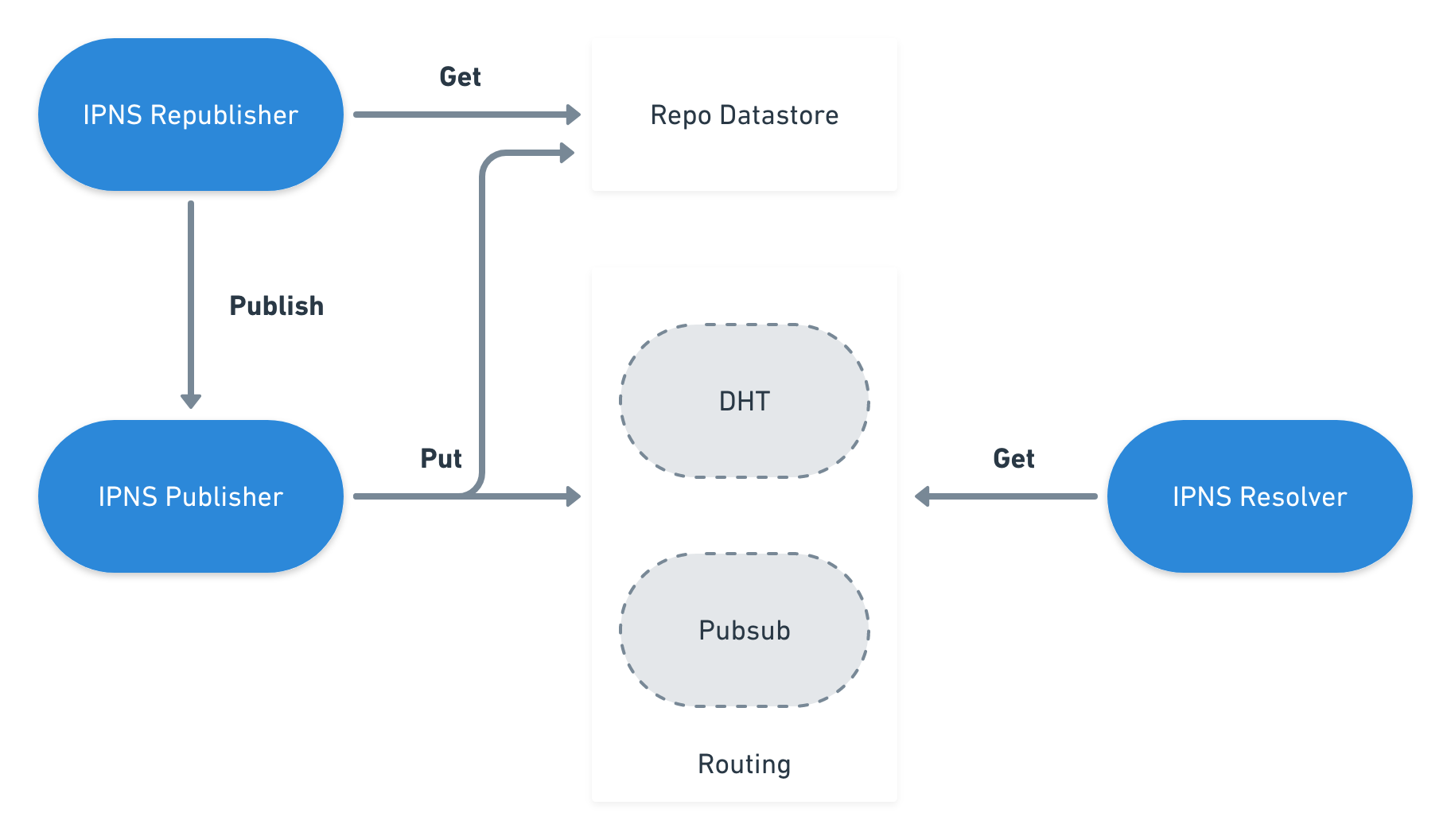
Taking into consideration a p2p network, each peer should be able to publish IPNS records to the network, as well as to resolve the IPNS records published by other peers.
When a node intends to publish a record to the network, an IPNS record needs to be created first. The node needs to have a previously generated asymmetric key pair to create the record according to the data structure previously specified. It is important pointing out that the record needs to be uniquely identified in the network. As a result, the record identifier should be a hash of the public key used to sign the record.
As an IPNS record may be updated during its lifetime, a versioning related logic is needed during the publish process. As a consequence, the record must be stored locally, in order to enable the publisher to understand which is the most recent record published. Accordingly, before creating the record, the node must verify if a previous version of the record exists, and update the sequence value for the new record being created.
Once the record is created, it is ready to be spread through the network. This way, a peer can use whatever routing system it supports to make the record accessible to the remaining peers of the network.
The means of distribution are left unspecified. Implementations MAY choose to
publish signed record using multiple routing systems, such as
libp2p Kademlia DHT or [ipns-pubsub-router] (see Routing record).
On the other side, each peer must be able to get a record published by another node. It only needs to have the unique identifier used to publish the record to the network. Taking into account the routing system being used, we may obtain a set of occurrences of the record from the network. In this case, records can be compared using the sequence number, in order to obtain the most recent one.
As soon as the node has the most recent record, the signature and the validity must be verified, in order to conclude that the record is still valid and not compromised.
Finally, the network nodes may also republish their records, so that the records in the network continue to be valid to the other nodes.
5.2 Record Creation
IPNS record MUST be serialized as IpnsEntry protobuf, and IpnsEntry.data
MUST be signed (IpnsEntry.signatureV2) using the private key.
Creating a new IPNS record MUST follow the below steps:
-
Create IpnsEntry protobuf
-
Create a DAG-CBOR document with values for Value, Validity,
ValidityType, Sequence, and TTL
-
Following DAG-CBOR specification is paramount.
The CBOR bytes will be used for signing and the serialized form must be
deterministic.
-
If you are updating an existing record, remember to increase values in
sequence and validity
-
Store DAG-CBOR in IpnsEntry.data.
-
If you want to store additional metadata in the record, add it under
unique keys at IpnsEntry.data.
-
The order of fields impacts signature verification. If you are using an
alternative CBOR implementation, make sure the CBOR field order follows
[rfc7049] sorting rules: length and then bytewise. The order of
fields impacts signature verification.
-
If your public key can't be inlined inside the IPNS Name, include a
serialized copy in IpnsEntry.pubKey
- This step SHOULD be skipped for Ed25519, and any other key types that are
small enough (32 bytes) to be inlined inside IPNS Name itself.
-
Create IpnsEntry.signatureV2
-
Create bytes for signing by concatenating ipns-signature: prefix (bytes
in hex: 69706e732d7369676e61747572653a) with raw CBOR bytes from
IpnsEntry.data
-
Sign concatenated bytes from the previous step using the private key, and
store the signature in IpnsEntry.signatureV2
-
Confirm that the serialized IpnsEntry bytes sum to less than or equal to
the size limit.
Created IpnsEntry protobuf includes signed data CBOR and optional public key:
message IpnsEntry {
optional bytes pubKey = 7;
optional bytes signatureV2 = 8;
optional bytes data = 9;
}
The IpnsEntry.data CBOR document includes key-value pairs for Value,
Validity, ValidityType, Sequence and TTL.
Keys are sorted and serialized in order that follows
the DAG-CBOR specification:
// IpnsEntry.data
{
Sequence: …
TTL: …
Validity: …
ValidityType: …
Value: …
}
5.2.1 Record Creation with Legacy SignatureV1
Fields related to signatureV1 has been deprecated since 2021.
V1 signatures are no longer used during record validation.
However, it may be necessary to create a V2+V1 record that allows legacy
software to use IPNS to upgrade itself to the latest version which supports V2
signatures. In such case, follow the steps below.
- Create
IpnsEntry and set value, validity, validityType, sequence, and ttl
- If you are updating an existing record, remember to increase values in
sequence and validity
- Create a DAG-CBOR document with the same values for
Value, Validity, ValidityType, Sequence, and TTL
- This is paramount: this CBOR will be used for signing.
- Store DAG-CBOR in
IpnsEntry.data.
- If you want to store additional metadata in the record, add it under unique keys at
IpnsEntry.data.
- The order of fields impacts signature verification. If you are using an alternative CBOR implementation, make sure the CBOR field order follows [rfc7049] sorting rules: length and then bytewise. The order of fields impacts signature verification.
- If your public key can't be inlined inside the IPNS Name, include a serialized copy in
IpnsEntry.pubKey
- This step SHOULD be skipped for Ed25519, and any other key types that are inlined inside IPNS Name itself.
- Create
IpnsEntry.signatureV2
- Create bytes for signing by concatenating
ipns-signature: prefix (bytes in hex: 69706e732d7369676e61747572653a) with raw CBOR bytes from IpnsEntry.data
- Sign concatenated bytes from the previous step using the private key, and store the signature in
IpnsEntry.signatureV2
- Create
IpnsEntry.signatureV1 (backward compatibility, for legacy software)
- Create bytes for signing by concatenating
IpnsEntry.value + IpnsEntry.validity + string(IpnsEntry.validityType)
- Sign concatenated bytes from the previous step using the private key, and store the legacy signature in
IpnsEntry.signatureV1
- Confirm that the serialized
IpnsEntry bytes sum to less than or equal to the size limit.
5.3 Record Verification
Implementations MUST resolve IPNS Names only using verified records.
Record's data and signature verification MUST be implemented as outlined below, and fail on the first error.
- Before parsing the protobuf, confirm that the serialized
IpnsEntry bytes sum to less than or equal to the size limit.
- Confirm
IpnsEntry.signatureV2 and IpnsEntry.data are present and are not empty
- Extract public key
- Use
IpnsEntry.pubKey or a cached entry in the local key store, if present.
- If public key is missing
- Assume the public key is inlined in the IPNS Name itself (e.g., Ed25519 inlined using
identity multihash)
- Confirm Multihash type is
identity
- Unmarshall public key from Multihash digest
- Deserialize
IpnsEntry.data as a DAG-CBOR document
- Create bytes for signature verification by concatenating
ipns-signature: prefix (bytes in hex: 69706e732d7369676e61747572653a) with raw CBOR bytes from IpnsEntry.data
- Verify the signature in
IpnsEntry.signatureV2 against the concatenated result from the previous step.
- If
IpnsEntry.signatureV1 or IpnsEntry.value is present, confirm the values in IpnsEntry protobuf match deserialized ones from IpnsEntry.data:
IpnsEntry.value must match IpnsEntry.data[Value]IpnsEntry.validity must match IpnsEntry.data[Validity]IpnsEntry.validityType must match IpnsEntry.data[ValidityType]IpnsEntry.sequence must match IpnsEntry.data[Sequence]IpnsEntry.ttl must match IpnsEntry.data[TTL]
- Check
Validity
- If
ValidityType is 0 (EOL) parse the Validity as an ASCII string
that follows notation from [rfc3339]
(1970-01-01T00:00:00.000000001Z) and confirm it is bigger than the
current time.
Value from IpnsEntry.signatureV1 MUST never be used for signature verification.
Implementations MUST ensure IpnsEntry.signatureV2 is used instead.
Value from IpnsEntry.value MUST never be used unless it is the same as signed IpnsEntry.data[Value].
